Difference between revisions of "Check a Downloaded ISO Image For Errors"
Views
Actions
Namespaces
Variants
Tools
imported>Verityproductions (Created page with "= Overview = Prior to burning your downloaded ISO image (or using it as a virtual disc in Virtualbox), it is '''strongly''' recommended that you first check that it hasn't be...") |
Des Kitten (talk | contribs) m (Variant to checking in Windows using powershell) Tags: Mobile web edit Mobile edit |
||
| (44 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
<languages/> | |||
__TOC__ | |||
Prior to burning your downloaded ISO image (or using it as a virtual disc in Virtualbox), it is '''strongly''' recommended that you first check that it hasn't been corrupted | {{SectionTemplate| | ||
1=<translate><!--T:1--> Overview</translate>| | |||
2=<translate><!--T:2--> | |||
Prior to burning your downloaded ISO image (or using it as a virtual disc in Virtualbox), it is '''strongly''' recommended that you first check that it hasn't been corrupted. The consequences of not doing so, especially if you intend on installing Manjaro as your main operating system, should be obvious, that is that a corrupted image will result in a corrupted installation. | |||
To | <!--T:3--> | ||
To make the check, you must first download the appropriate ''checksum file'' from the same ''Sourceforge'' website folder as your chosen ISO image. A checksum file will have the same name as the ISO image that it is to be used with; the only difference is that it will end in either '''-sha1.sum''' or '''-sha256.sum'''. For example, the appropriate checksum files for the ''manjaro-xfce-0.8.1-x86_64.iso'' file (64 bit Manjaro release 0.8.1 with the XFCE desktop) would be: | |||
<!--T:4--> | |||
* manjaro-xfce-0.8.1-x86_64'''-sha1.sum''', and/or | |||
* manjaro-xfce-0.8.1-x86_64'''-sha256.sum'''</translate>| | |||
3=BigManjaroIcon.png | |||
}} | |||
The checksum file | {{SectionTemplate| | ||
1=<translate><!--T:5--> SHA1 and SHA256</translate>| | |||
2=<translate><!--T:6--> | |||
The 'sha' part of the checksum file name stands for <u>S</u>ecure <u>H</u>ash <u>A</u>lgorithm. This algorithm is used to generate a particular code unique to the downloaded ISO image. '''sha1''' and '''sha256''' are different versions of the algorithm that you can use to do this. Whilst sha1 is the most commonly used version, sha256 is a later and more secure version. Whichever you decide to use is entirely your choice. '''However, if you are unsure, then it is recommended to use sha256'''. | |||
<!--T:7--> | |||
The checksum file itself is just a text document that contains a code that should match the code generated by the sha1 or sha256 algorithm. As such, if the code generated from the ISO file matches that contained in the checksum file, then the ISO is fine; otherwise, if the two codes don't match then it means that the ISO file has changed in some way, most likely due to being corrupted. You can think of it like someone using a secret password to identify who they are: if they provide the wrong password, then something is obviously amiss! | |||
<!--T:8--> | |||
Don't worry if this all sounds a bit much, it's actually very straightforward and easy to use!</translate> | |||
}} | |||
= | {{SectionTemplate| | ||
1=<translate><!--T:9--> Checking in Linux</translate>| | |||
2=<translate> | |||
<!--T:10--> | |||
To check the integrity of your downloaded file, it will be necessary to first open the downloaded checksum file using a text editor such as ''Gedit''. Depending on whether you intend to use sha1 or sha256, ensure that you have downloaded and opened the appropriate checksum file, that is one ending in *.sha1sum or *.sha256sum respectively) as they will contain different codes. Once the checksum file has been opened and the code is visible, open up your terminal and change to the directory where your downloaded ISO is stored. For example, if your ISO file is located in the default ''Downloads'' folder, you would enter the following command: | |||
<!--T:11--> | |||
{{UserCmd|command=cd Downloads}} | |||
<!--T:12--> | |||
The command to then perform a checksum uses the following syntax: | |||
<!--T:13--> | |||
[sha1sum or sha256sum] [ISO Image] | |||
<!--T:14--> | |||
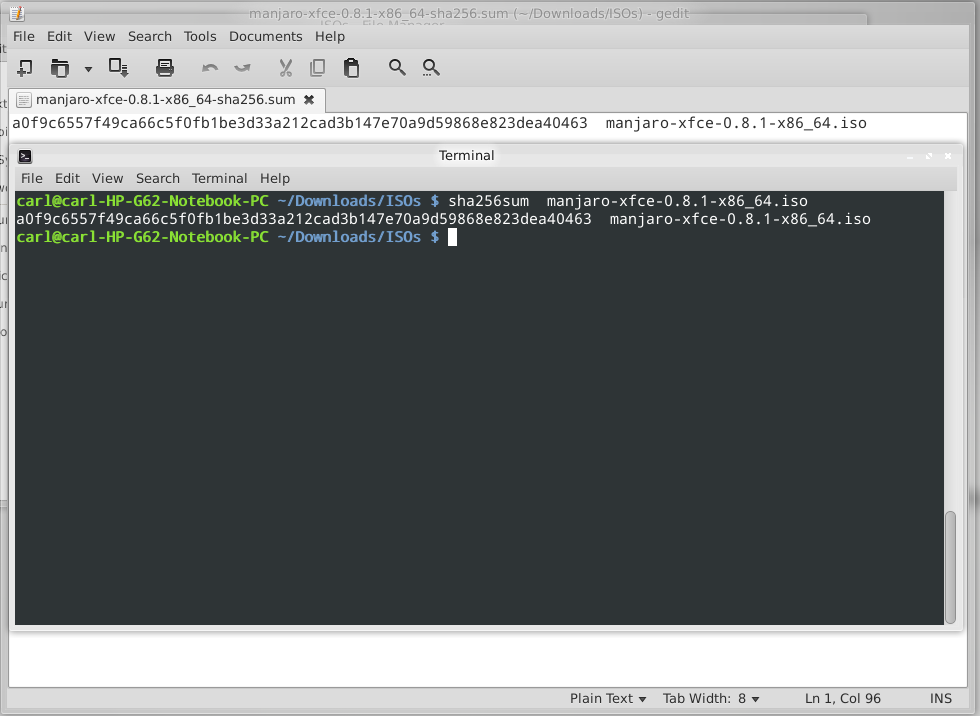
[[File: sha256.png|thumb|left|375px]] | |||
<!--T:15--> | |||
For example, the following command will use sha256 to generate a code from the 64 bit Manjaro XFCE 0.8.1 ISO. The code generated can then be compared to the code provided by the appropriate sha256 checksum file: | |||
<!--T:16--> | |||
{{UserCmd|command=sha256sum manjaro-xfce-0.8.1-x86_64.iso}} | |||
<!--T:17--> | |||
As illustrated, in this instance both codes match, thus confirming that the downloaded ISO file is correct. The following command would use sha1 to undertake exactly the same task: | |||
<!--T:18--> | |||
{{UserCmd|command=sha1sum manjaro-xfce-0.8.1-x86_64.iso}} | |||
<!--T:19--> | |||
When satisfied that both codes match, then it is safe to proceed to either burning the ISO to your chosen installation media, or using it immediately in Virtualbox. If the codes do not match, then it will be necessary to delete the ISO image and download it again. | |||
</translate> | |||
}} | |||
{{SectionTemplate| | |||
1=<translate><!--T:20--> Checking in Windows</translate>| | |||
2=<translate> | |||
<!--T:21--> | |||
[[File: wincheck.jpg|thumb|left|375px]] | |||
<!--T:22--> | |||
It will be necessary to download and install a checksum utility application. There are many tools which can provide sha1 and sha256 sums. One such tool is '''[https://github.com/tedsmith/quickhash Quick Hash]''' | |||
</translate> | |||
<br clear="all" /> | |||
}}Also, here is another way: | |||
1) Press Win+R, and enter 'powershell'. (Also you can press the the magnifying glass icon near the Start button, and enter same word.) | |||
2) In opened shell console, using command 'cd' go to the folder wherein you have been downloaded the manjaro-xxxx.iso file. | |||
Example: PS C:\Windows\System32> cd D:\Downloads\ | |||
= | 3) Write the command: <syntaxhighlight lang="console"> | ||
certutil -hashfile .\manjaro-gnome-22.1.3-230529-linux61.iso SHA512 | |||
</syntaxhighlight>It will calculate the hash sum which you can compare with that consists in downloaded Checksum file (.iso.SHA512) that you can open with notepad.{{SectionTemplate|<translate><!--T:23--> See Also</translate>| | |||
* '''[[How-to verify GPG key of official .ISO images]]''' | |||
* '''[[Download Manjaro]]''' | |||
* '''[[Burn an ISO File]]''' | |||
* '''[[Installation Guides]]'''|Chmsee-icon.png}} | |||
[[Category:Contents Page{{#translation:}}]] | |||
Latest revision as of 10:59, 15 June 2023
To make the check, you must first download the appropriate checksum file from the same Sourceforge website folder as your chosen ISO image. A checksum file will have the same name as the ISO image that it is to be used with; the only difference is that it will end in either -sha1.sum or -sha256.sum. For example, the appropriate checksum files for the manjaro-xfce-0.8.1-x86_64.iso file (64 bit Manjaro release 0.8.1 with the XFCE desktop) would be:
- manjaro-xfce-0.8.1-x86_64-sha1.sum, and/or
- manjaro-xfce-0.8.1-x86_64-sha256.sum
The checksum file itself is just a text document that contains a code that should match the code generated by the sha1 or sha256 algorithm. As such, if the code generated from the ISO file matches that contained in the checksum file, then the ISO is fine; otherwise, if the two codes don't match then it means that the ISO file has changed in some way, most likely due to being corrupted. You can think of it like someone using a secret password to identify who they are: if they provide the wrong password, then something is obviously amiss!
Don't worry if this all sounds a bit much, it's actually very straightforward and easy to use!The command to then perform a checksum uses the following syntax:
[sha1sum or sha256sum] [ISO Image]
For example, the following command will use sha256 to generate a code from the 64 bit Manjaro XFCE 0.8.1 ISO. The code generated can then be compared to the code provided by the appropriate sha256 checksum file:
As illustrated, in this instance both codes match, thus confirming that the downloaded ISO file is correct. The following command would use sha1 to undertake exactly the same task:
When satisfied that both codes match, then it is safe to proceed to either burning the ISO to your chosen installation media, or using it immediately in Virtualbox. If the codes do not match, then it will be necessary to delete the ISO image and download it again.
It will be necessary to download and install a checksum utility application. There are many tools which can provide sha1 and sha256 sums. One such tool is Quick Hash
Also, here is another way:
1) Press Win+R, and enter 'powershell'. (Also you can press the the magnifying glass icon near the Start button, and enter same word.)
2) In opened shell console, using command 'cd' go to the folder wherein you have been downloaded the manjaro-xxxx.iso file.
Example: PS C:\Windows\System32> cd D:\Downloads\
3) Write the command:
certutil -hashfile .\manjaro-gnome-22.1.3-230529-linux61.iso SHA512
It will calculate the hash sum which you can compare with that consists in downloaded Checksum file (.iso.SHA512) that you can open with notepad.